CASB for enterprise hosting entire infrastructure on
written by: NetworkFort Team, info@networkfort.com
In this modern era, all our enterprises, either big or small, have something hosted. Now the question pops up in our minds that what is getting hosted and where it is getting hosted. Sometimes, all our services like database, email are with a single hosting company, or sometimes, enterprises share server space with some other company. Those servers are generally cloud-based. And if these are cloud-based then, whether the data is secured or not. These questions and their complete understanding will render you more aware of your hosting infrastructure and, eventually, you would have more control over it.
A Hosting Infrastructure
Hosting infrastructure can be categorized as managed or unmanaged hosting infrastructure. In the former category, hosting infrastructure is the one in which some outside provider provides the OS while the enterprise maintains its application and services. In the latter category, the external provider not only provides OS but also server space with all the applications and pertinent services and required security. The other leveraged aspects of managed hosting infrastructure are; dedicated hosting, shared hosting, public cloud hosting, and private cloud hosting.
- Dedicated Hosting(each client has their infrastructure and server)
- Physical shared hosting (multiple clients are communally hosted)
- Public clouds (multiple clients share virtualized resources)
- Private Cloud Hosting (scalable resources dedicated to a single client.

Cloud-based hosting and Cybersecurity:
The contemporary workplace and workforce are cloud-based and remotely distributed that is a chief target for hackers. With the escalating technical sophistication of cybercriminals and hackers, cloud apps security and data loss prevention has become very critical nowadays. The cybersecurity world is tied inextricably to the latest computing services and an explicit trend towards cloud computing has been observed in the cybersecurity world. Adaption towards the cloud can increase business agility, flexibility, and efficiency, but it also hurls a threat to cybersecurity because cyber criminals can break into user accounts to attack funds and data.
Limitations of Cloud Security:
While playing a salient role in providing security to customers, cloud security has some limitations too. The first and foremost limitation is a lack of control and flexibility at the user end over their data. Sometimes, users are not even capable of transferring their data to some other providers because providers may not exhibit Interoperability. Lack of privacy is another notable limitation that involves some exposure of information to the provider (CSP) to utilize all the services which hinder the privacy of users. Sometimes, these providers accumulate such a large number of data that attracts hackers and attackers. In addition to all this, cloud computing demands robust credential management that must be capable of secure logins to implement various cloud services from multiple devices that are troublesome a lot.
Statistics of Cloud Security breaches:
A significant number of companies have installed some degree of cloud infrastructure services (IaaS, PaaS, FaaS, or serverless) with the general concern of security breach. With the rising complexity, these services demand adequate cloud security that has become very difficult nowadays because breaches of cloud security run rampant. Unfortunately, numerous breaches have been reported in 2019 March alone like the revealing of thousands of doctors’ notes by Meditab, 1.5 million customer records by Gearbest, 2.4 million client records from Dow Jones, and 809 million customers records by verifications. All these breaches were the result of misconfigurations done by Cloud Service Provider (CSP) customers
CASB is an ultimate solution
What is Cloud App Security Broker (CASB):
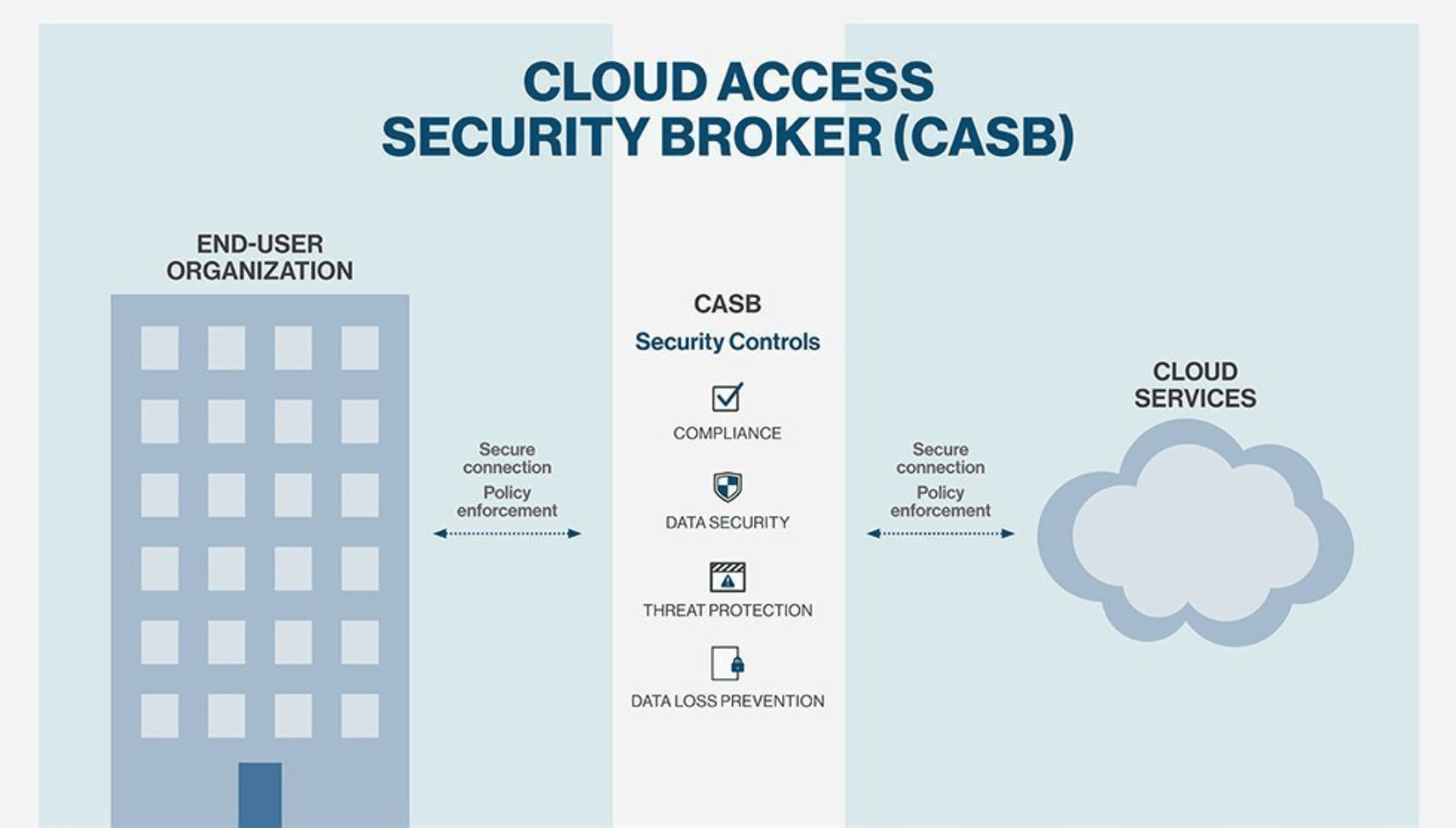
CASB is a cyber-security software tool that operates within an organization’s on-premises. It operates between users and cloud services applications and resources to help monitor and implement security policies for every single cloud application. Multiple parameters play their parts to make CASB work. The very crucial is the implementation of API support for a cloud app, CASB implements the API of every unique app that is accessed by users.
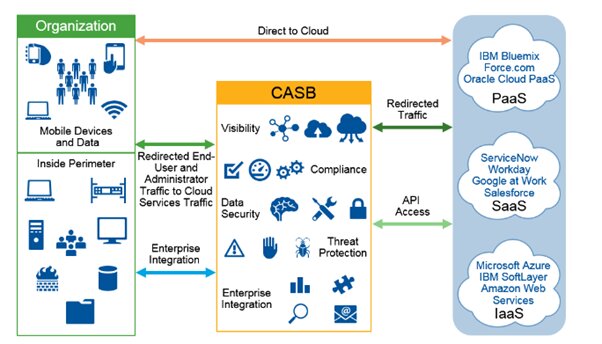
Why does an organization need a CASB? Key features of CASB:
A large number of features have been listed since the inception of CASB. The most fundamental features are granting compliance, resolving data security issues, and preventing data loss because CASB scrutinizes all the data like original files and documents. It also provides advanced and added threat protection that senses very sophisticated viruses and threats. Furthermore, it allows visibility into sanctioned apps accessed by users and this feature has attracted several organizations to install CASB. Finally, CASBS also enables viewing the cloud application usage so that overuse and misuse can be monitored and mitigated with the right plan.
Four fundamental pillars of Cloud Access Security Brokers:
The four fundamental pillars of Cloud Access Security Brokers are:
1. Visibility:
CASB helps to highlight the hidden and unknown risks. It helps to reveal ‘shadow IT’; those processes and cloud services that are not reported on the system and may introduce threats.
2. Threat Protection:
It protects all the attacks outside or inside and reports all the data leakages. Some of the techniques might help in blocking cyber-attacks like sandboxing, browser insulation, or anti-malware detection.
3. Data Security:
CASB provides supreme protection against all the private data and maintains the integrity of the data. For this purpose, ‘access control’ or ‘data loss prevention’ can be used.
4. Compliance:
Compliance has become a crucial issue to mitigate for the companies using the cloud because the cloud is not managed under one specific supervision. These companies find it arduous to meet the compliance requirements like HIPAA, GDPR. In case of non-compliance, these companies have to face some sort of penalties. In this regard, CASBs provide support to store data in the form of cloud regulatory compliance so that these companies run businesses efficiently.
Services CASB provides:
Following cloud services are listed below:
● Saas ( Software as a service)
● IaaS ( Infrastructure as a service)
● PaaS ( Platform as a service)
Want to secure your data with networkfort?
To mitigate all the threats mentioned above, networkfort will provide security to all the cloud applications such as Microsoft 365, Google G Suite, Box, Zoom, Salesforce, Workday, and more with appropriate adaptive controls for the security access to all the cloud apps. It will also protect from account compromise, oversharing of data, and compliance risks in the cloud. Other paramount features it offers are people-centric visibility to threats and automated response capabilities that would be delivered by our highly skilled researchers. Moreover, its analytical team considers all the risk factors, applies all risk-based controls including step-up authentication and VPN enforcement, and also enables providing third-party add-on apps and adaptive levels of access to users.
The expertise of Networkfort:
Our CASB provides a remarkable protection tool that makes any enterprise able to align its set policy, monitoring behavior, compliance management, threat protection, data security, and risk management. It also strengthens the enterprise’s visibility into all authorized and unauthorized cloud operations. Furthermore, it also has the capability to monitor and intercept data traffic between the enterprise’s network and cloud platform.
 please click on the website networkfort.com for further details.
please click on the website networkfort.com for further details.